Category: Ubuntu 12.04
Tomcat CatchAll (Hosts)
Re: Several hosts within one tomcat / catch-all problem 2010-11-21 20:08
Hi Konstantin,
>BTW, you can put those names in an external file and use it in the
>server.xml as an XML entity. Like the example in
>http://wiki.apache.org/tomcat/FAQ/Password
Inspired by this thread and having a similar issue in maintaining virtual host aliases I edited my server.xml as follows:
I added this before the <Server>.
<!DOCTYPE aliases-xml [
<!ENTITY aliases SYSTEM "/path/to/network/storage/aliases.txt">
]>
I moved my <Alias> tags to /path/to/network/storage/aliases.txt, substituting &aliases;
This works very well. Thanks!
>and use JMX or call mapper.addHostAlias(..) directly to add aliases
>programmatically at runtime. (though there is no guarantee that the
>Mapper API does not change between Tomcat minor releases).
I investigated what an implementation of this might look like at a higher level. In looking through the Tomcat interfaces it looks like this is similar to the notion of automatically creating Context for users with a UserConfig listener.
It would be an AliasConfig class extending HostConfig.
<Listener className="my.web.server.listener.package.AliasConfig" aliases="/path/to/alias/file"/>
Then in the start event function it is as simple as "host.addAlias(subDomainName);" for each alias found in the aliases file.
Does this make sense?
Regards,
Dave
Tomcat and Apache Setup – With LB
Tomcat and Apache Setup
My example at bottom…
Most Tomcat configurations are a Apache/Tomcat setup, Apache serving up the static content and then passing any JSP to Tomcat to process. Tomcat can be integrated with Apache by using the JK Connector. The JK Connector uses the Apache JSserv Protocol (AJP) for communications between Tomcat and Apache.
The AJP Connector
The AJP protocol is used for communication between Tomcat and Apache, the software modules used on Apache are mod_jk or mod_proxy. Both are native code extension modules written in C/C++, on the Tomcat side the software module is the AJP Connector written in Java.
The below diagram shows how the native code Apache module (mod_jk or mod_proxy) works with Tomcat. Apache will receive the incoming JSP or servlet request and using the Apache module will pass this request via the AJP protocol to Tomcat, the response will also be sent back to the Apache server via the AJP protocol.
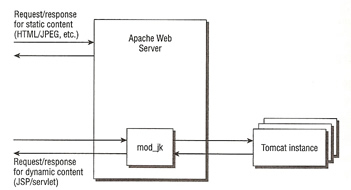
The Apache JServ Protocol (AJP) uses a binary format for transmitting data between the Web server and Tomcat, a network socket is used for all communication. The AJP packet consist of a packet header and a payload, below is the structure of the packet
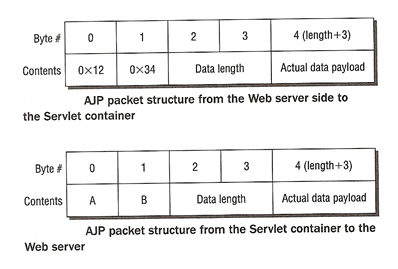
As you can see, the binary packet starts with the sequence 0X1234, this is followed by the packet size (2 bytes) and then the actual payload. On the return path the packets are prefixed by AB (the ASCII codes for A and B), the size of the packet and then the payload.
The major feature of this protocol are
- Good performance on fast networks
- Support for SSL, encryption and client certificate
- Support of clustering by forwarding requests to multiple Tomcat 6 servers
One of the ways the AJP protocol reduces latency is by making the Web server reuse already open TCP-level connections with Tomcat. This saves the overhead of opening a new socket connections for each request, its a bit like a connection pool.
The configuration of a AJP Connector is below
| AJP Connector example | <Connector port="8009" protocol="AJP/1.3" redirectPort="8443" /> |
A worker represents a running instance of Tomcat, a worker serves the requests for all dynamic web components. However you can run multiple instances of Tomcat in a cluster to implement load balancing or site partitioning. Each worker is identified by a unique hostname or a unique IP address and port number. You may what to implement multiple workers for the following reasons
- When you want different Web application contexts to be served by different Tomcat workers
- When you want different virtual hosts to be served by different Tomcat workers
- When you want to service more requests than the capacity of a single physical server
To let Apache know where the Tomcat servers are a file called workers.properties is created detailing this information. I describe this file next
|
Worker List
|
|
| Attribute | Description |
| work.list |
Describe the workers that are available to Apache via a list
|
|
Worker Types
|
|
| Attribute | Description |
| ajp13 |
This type of worker represents a running Tomcat instance
|
| lb |
used for load balancing
|
| status |
display useful information about how the load among the various Tomcat workers is distributed
|
| jni |
Used in process, this worker handles the forwarding of requests to in-process Tomcat workers using JNDI
|
| ajp12 |
worker that support the AJP 1.2 protocol
|
|
Other Worker Properties
|
|
| Attribute | Description |
| worker.test1.type | Describes the type of worker (see above for types) |
| worker.test1.host |
The host where the worker Tomcat instance resides
|
| worker.test1.port |
The port the AJP 1.3 Connector Tomcat instance is listening on (default 8009)
|
| worker.test1.connection_pool_size |
The number of connections used for this worker to be kept in a connection pool
|
| worker.test1.connection_pool_minsize |
The minimum number of connections kept in a connection pool
|
| worker.test1.connection_pool_timeout |
The number of seconds that connections to this worker should be left in the connection before expiry |
| worker.test1.mount | The contexts paths that are serviced by the worker, you can also use the JkMount directive in the http.conf file |
| worker.test1.retries |
Controls the number of times mod_jk will retry when a worker returns a error
|
| worker.test1.socket_timeout |
controls how long a worker will wait for a response on a socket before indicating an error
|
| worker.test1.socket_keepalive | indicates if the connection to the worker should be subject to keep alive |
| worker.test1.lbfactor |
An integer indicating the local-balance factor used by the load balancer to distribute work between multiple instances of Tomcat.
|
|
Worker Loading Balancing Properties
|
|
| Attribute | Description |
| worker.bal1.balance_workers | A list of workers to load balance between |
| worker.bal1.lock | The type of locking used O (Optimistic) or P (Pessimistic) |
| worker.bal1.method |
can be set to R (Requests), T (Traffic), B (Busy-ness)
R = The worker to use is based on the number of requests forwarded |
| worker.bal1.secret | Sets a default secret password for all workers |
| worker.bal1.sticky_session |
Tells the mod_jk to respect the sessionID in the request and ensures that the same session is always serviced by the same worker instance.
|
| worker.bal1.sticky_session_force | This is used for failover |
|
Example
|
|
| Simple example | worker.list = worker1 worker.worker1.type = ajp13 worker.worker1.host = 192.168.0.1 worker.worker1.port = 9009 worker.worker1.connection_pool_size = 5 worker.worker1.connection_pool_timeout = 300 |
| Load Balancing example |
worker.list = loadbal1,stat1 Note: if one of your servers is a slow server then lower the lbfactor of that server |
There are a number of Apache directives that you can configure in the httpd.conf file
|
Apache mod_jk Directives
|
|||||||||||||||||||||
| Directive | Description | ||||||||||||||||||||
| JkWorkerFile | tells mod_jk where to find the workers property file | ||||||||||||||||||||
| JkLogFile | tells mod_jk where to write its logs | ||||||||||||||||||||
| JkLogLevel | sets the level of logging (info, error or debug) | ||||||||||||||||||||
| JkRequestLogFormat | specifies the log format, below are the options that you can use
|
||||||||||||||||||||
| JkMount | control the URL matching and forwarding to the Tomcat workers | ||||||||||||||||||||
|
Example
|
|||||||||||||||||||||
| JkWorkerFile | JkWorkerFile conf/worker.properties | ||||||||||||||||||||
| JkLogFile | JkLogFile /var/logs/httpd/mod_jk.log | ||||||||||||||||||||
| JkLogLevel | JkLogLevel debug | ||||||||||||||||||||
| JkRequestLogFormat | JkRequestLogFormat "%w %U %T" | ||||||||||||||||||||
| JkMount | JkMount /examples/jsp/* worker1 | ||||||||||||||||||||
SSL provides a secure connection between Tomcat and Apache, the steps involved in getting this working are
- Install OpenSSL on your server
- Check that Apache has mod_ssl support
- Get or generate a SSL certificate and install it into Apache
- Test the SSL-enabled Apache-Tomcat setup
To make sure that you have openssl installed and the mod_ssl modules installed in Apache run the following
| Check foe OpenSSL | # openssl version |
| Check for Apache module mod_ssl | # <apache path>/httpd -D DUMP_MODULES |
If any of these are not installed then I recommend you download the latest version and install as per the Installation guides.
There are a number of steps to generate a test certificate using OpenSSL
- Create the configuration file for generating the certificate
- Create a certificate signing request, this is what you send to the CA if you are buying a certificate
- Remove the passphrase from the private key
- Purchase a certificate from a CA or create a self-signed certificate
- Install the key and certificate to the Apache server
Below are the steps to creating your own cert
| step 1 |
Create a working directory called certs
RANDFILE = ./random.txt Create a random file called random.txt put a large number in it |
| step 2 |
Now create the certificate Two files should have been created server.csr and keyfile.pem |
| step 3 | Now remove the passphrase from the private key # openssl rsa -in keyfile.pem -out server.key |
| step 4 |
Now create a self-signed certificate # openssl X509 -in server.csr -out server.crt -req -signkey server.key -days 365 Note: in a production environment the certificate signing request file generated (server.csr) is sent to a Certificate Authority and a certificated purchased |
| step 5 | Last but not least copy the server.key and server.crt in to the Apache conf directory |
To setup the mod_ssl in Apache you need to perform the following in Apache httpd.conf file
| include the httpd-ssl.conf | include conf/extra/httpd-ssl.conf |
| Load the SSL modules | LoadModule ssl_module modules/mod_ssl.so |
| SSLCertificateKeyFile | set this attribute to the path to the server.key file |
| SSLCertificateFile | set this attribute to the path to the server.crt file |
Once all the above is completed you can now point your browser to the Apache server, hopefully the browser will pop up with a security alert (because of the self-signed certificate).
The only change to make the Apache-Tomcat setup is to change the <VirtualHost> attribute
| <VirtualHost> | <virtualHost _default_:443> …. JkWorkersFile …… JkMount …….. </VirtualHost> |
I will be discussing Tomcat clustering in a later topic will describes a more detailed viewing of load balancing and persistent sessions with-in-memory session replication but for this section I will discuss a basic load balancing solution.
The mod_proxy module can also be used for load balancing but will not be discussed here, the mod_jk module sup[ports load balancing with seamless sessions, it uses a simple round-robin algorithm. Each Tomcat worker is weighted in the worker.properties file which specifies how the request load is distributed between workers.
A seamless session is also known as session affinity or a sticky session. When a request is made any of the Tomcat instances is used, but any subsequent request will be routed to the same Tomcat instance. to keep the same user session.
The following steps are required to set up load balancing in Tomcat
- Change the CATALINA_HOME in the Tomcat startup files to point to different locations for each of the Tomcat instances
- Set different AJP Connector ports for the instances
- Disable the Coyote HTTP/1.1 Connector
- set the jvmroute in the Standalone Engine
- Configure the Tomcat worker in the workers.properties file.
One assumption I will be making here is that all the Tomcat instances will be running on the same server
The first step is to change the CATALINA_HOME variable in each of the startup.bat (Windows) or startup.sh (Unix) instances
| CATALINA_HOME |
set CATALINA_HOME=c:\apps\tomcatA Note: the other Tomcat instances would be tomcatB and tomcatC |
Now in each Tomcat instance we must set a different AJP Connector port number (server.xml)
| AJP Connector port |
<Connector port="8009" protocol="AJP/1.3" redirectPort="8443" /> Note: on the other Tomcat instances use ports 8010 and 8011 |
To avoid startup/shutdown port conflicts we must change each Tomcats worker server port (server.xml)
| server port |
<Server port="8005" shutdown="SHUTDOWN" debug="0"> Note: on the other Tomcat instances use ports 8006 and 8007 |
Because all the Tomcat instances will be running in conjunction with the load-balancer worker, it's possible that someone could directly access any of the available workers vioa the default HTTP Connector, by passing the load-balancer path. To avoid this comment out the HTTP Connector configuration of all the Tomcat instances (server.xml)
| disable HTTP Connector |
<!– Define |
An important step for load balancing is specifying the jvmRoute. The jvmRoute is an attribute of Engine directive that acts as an identifier for that particular Tomcat worker. The attribute must be unique across all Tomcat instances, this unique ID is used in the workers.properties file for identifying each Tomcat worker (server.xml).
| jvmRoute |
<Engine name="Standalone" defaultHost="localhost" jvmRoute="tomcatA" > Note: the other Tomcat instances would be tomcatB and tomcatC |
You will also need to comment out the Catalina Engine directive (server.xml)
| Catalina Engine disable |
<!– Define Note: the other Tomcat instances would be tomcatB and tomcatC |
In Apache's httpd.,conf file you need to add some load balancing directives, also make sure you have the module mod_jk loaded
| httpd.conf directives |
JkWorkersFile conf/worker.properties |
The last thing is to create the workers property file, i have already discuss this file above.
| worker.properties file |
worker.list = loadbal1,stat1 |
To test the load balancer and sticky sessions use the below JSP page (one for each instance), just place it in the webapps/examples/jsp directory.
| jsp test page |
<%@ page language="java" %> |
Use the below URL's for testing, etc. Don't forget to play around with the lbfactor on each Tomcat instance to see what affect it has.
| URL's |
http://local/examples/jsp/index.jsp |
==============================================
Be sure to update sample.com with new loadbalancer modJK
Don't forget to set your jvmRoute on each instance of TomCat within the server.xml
<Engine name="Catalina" defaultHost="localhost">–>
<Engine name="Catalina" defaultHost="localhost" jvmRoute="tc8xx">
==============================================
My Example located: vi /etc/libapache2-mod-jk/workers.properties
==============================================
#
# The workers that your plugins should create and work with
#
#worker.list=loadbalancer,status
#worker.list=loadbal1,stat1
worker.list=lb_tc8xx,lb_tc81x,stat1
#
#—— ajp13_worker WORKER DEFINITION ——————————
#———————————————————————
#
#
# Defining a worker named ajp13_worker and of type ajp13
# Note that the name and the type do not have to match.
#
worker.tc811.host=192.168.1.81
worker.tc811.port=8113
worker.tc811.type=ajp13
worker.tc812.host=192.168.1.81
worker.tc812.port=8123
worker.tc812.type=ajp13
worker.tc821.host=192.168.1.82
worker.tc821.port=8213
worker.tc821.type=ajp13
worker.tc822.host=192.168.1.82
worker.tc822.port=8223
worker.tc822.type=ajp13
#
# Specifies the load balance factor when used with
# a load balancing worker.
# Note:
# —-> lbfactor must be > 0
# —-> Low lbfactor means less work done by the worker.
worker.tc811.lbfactor=1
worker.tc812.lbfactor=1
worker.tc821.lbfactor=1
worker.tc822.lbfactor=1
#
# Specify the size of the open connection cache.
#worker.ajp13_worker.cachesize
#
#—— DEFAULT LOAD BALANCER WORKER DEFINITION ———————-
#———————————————————————
#
#
# The loadbalancer (type lb) workers perform wighted round-robin
# load balancing with sticky sessions.
# Note:
# —-> If a worker dies, the load balancer will check its state
# once in a while. Until then all work is redirected to peer
# workers.
# workers.
#Method — can be set to R (Requests), T (Traffic), B (Busy-ness)
# R = The worker to use is based on the number of requests forwarded
# T = The worker to use is based on the traffic that had been sent to the workers
# B = The worker to use is based on the load dividing the number of concurrent requests by the load factor
#setup the load-balancer
worker.lb_tc8xx.type=lb
worker.lb_tc8xx.method=R
worker.lb_tc8xx.balance_workers=tc811,tc812,tc821,tc822
worker.lb_tc8xx.sticky_session=True
###(This will generate a 500 instead of rerouting to a new server)
#worker.loadbalancer.sticky_session_force=True
worker.lb_tc81x.type=lb
worker.lb_tc81x.method=R
worker.lb_tc81x.balance_workers=tc811,tc812
worker.lb_tc81x.sticky_session=True
###(This will generate a 500 instead of rerouting to a new server)
#worker.loadbalancer.sticky_session_force=True
# Status worker for managing load balancer
worker.stat1.type=status
Tomcat with Apache2 VirtualHost AJP (mod_jk)
Tomcat changes:
You should be able to visit http://yourip:8080/manager/html and the below:
- http://192.168.1.81:8100/
- http://192.168.1.81:8110/
- http://192.168.1.81:8120/
- http://192.168.1.82:8200/
- http://192.168.1.82:8210/
- http://192.168.1.82:8220/
Deploy your tomcat application sample.war (433.79 kb) using the manager.
Note down the deployed application name (sample).
Edit /etc/tomcat7inst/8xx/conf/server.xml with following lines AFTER the ending </Host> tag, and BEFORE the ending </Engine> tag, insert the following:
<!– sample.com (here the appname is derived from the deploy above)–><Host name="www.sample.com" appBase="webapps" unpackWARs="true" autoDeploy="true">
<Alias>sample.com</Alias>
<Context path="" docBase="sample" debug="0" reloadable="true"/>
</Host>
Find the following in the same file (server.xml) and uncomment by removing <!– and –>
< !–
<Connector port=”8009″ protocol=”AJP/1.3″ redirectPort=”8443″ />
–>
<Connector port="8xx8" protocol="AJP/1.3" redirectPort="8443" />
Edit /etc/tomcat7inst/880/bin/startup.sh
export JAVA_OPTS="
-Dcom.qbw.instance=880
-Xms1g -Xmx1g -XX:MaxPermSize=128m
-Djava.rmi.server.hostname=192.168.1.186
"
Issue following the following command to activate the tomcat virtual host settings:
/etc/init.d/tomcat8xx stop
/etc/init.d/tomcat8xx start
Apache2 changes with load balancer:
Install the modjk module using following commad:
apt-get install libapache2-mod-jk
Files created:
- /etc/libapache2-mod-jk/workers.properties
- /var/log/apache2/mod_jk.log
- /var/log/apache2/jk-runtime-status
Edit /etc/libapache2-mod-jk/workers.properties
#workers.tomcat_home=/usr/share/tomcat6 #workers.java_home=/usr/lib/jvm/default-java # Change to your port worker.ajp13_worker.port=8108 #Change to your Tomcat IPworker.ajp13_worker.host=192.168.1.126
worker.ajp13_worker.type=ajp13
Create a apache2 virtualhost for eg. sample.com.conf with following contents on it.
<VirtualHost *:80>ServerName www.sample.com
ServerAlias sample.com ServerAdmin webmaster@sample.com JkMount /* ajp13_worker CustomLog /srv/www-logs/sample.com.access.log combined
ErrorLog /srv/www-logs/sample.com.error.log
</VirtualHost>
<VirtualHost sample.com:80>
ServerName sample.com
ServerAlias sample.com
DocumentRoot /var/lib/tomcat6/webapps/appname/
<Directory /var/lib/tomcat6/webapps/appname/>
Options FollowSymLinks Indexes
AllowOverride None
</Directory>
JkMount /* ajp13_worker
</VirtualHost>
Save conf file
Enable site:
cd /etc/apache2/sites-available
a2ensite sample.com.conf
Restart apache2 with following command /etc/init.d/apache2 restart
Update your hosts file to point sample.com to ip 192.168.1.186 (apache server ip)
Figures crossed. If every is followed as specified, the tomcat webapp deployed as appname shall be visible in your browser as simple apache2 page such as http://abc.com as opposed to http://abc.com:8080
Benefit: From now on, we just need to deploy the tomcat application and finally apache2 virtualhost creation followed by a restart to activate the new settings.
Disable Ctrl + Alt + Del
# sudo vi /etc/init/control-alt-delete.conf
Output
# control-alt-delete - emergency keypress handling## This task is run whenever the Control-Alt-Delete key combination is# pressed, and performs a safe reboot of the machine.description "emergency keypress handling"author "Scott James Remnant "start on control-alt-deletetaskexec shutdown -r now "Control-Alt-Delete pressed"
Change the following line
exec shutdown -r now "Control-Alt-Delete pressed"
To
#exec shutdown -r now "Control-Alt-Delete pressed"
SFTP over SSH
Ubuntu SFTP-Only Account How-to
This guide will show you how to setup Linux user accounts restricted to using SFTP only. These accounts will be unable to run arbitrary shell commands on the server or access/create files outside their own home directories. The steps in this guide were tested on Ubuntu Server 12.04 with version 5.3p1 of the OpenSSH daemon, obtained from the Ubuntu software repositories.Although this guide is aimed at Ubuntu users, it should also be applicable to other flavors of Linux as well. The most important factor to consider is the version of OpenSSH you have installed on your system. Version 5.0 or above is recommended as these versions support the OpenSSH ChrootDirectory configuration option that we’ll be using here.
Right, that’s enough of the rambling, let’s get to it…
Step 0 – Make sure /home is owned by ROOT
sudo chown root:root /home/
Step 1- Create a Group for the Restricted Accounts
For the sake of this example, we’ll create a new group called ‘sftponly‘ It’s best to use the addgroup command to do this, as it takes care of allocating an un-used GID (Group Identifier) to the new group for us:
sudo addgroup sftponly
Step 2- Create the User Account
For examples sake, we’ll create a user account with the username ‘raq3785‘ , set his home directory as ‘/home/raq3785‘ and give him the password ‘pass‘
We’ll use the useradd command here as it takes care of assigning an unallocated UID to the user account for us.
Creating the User Account:
sudo useradd -d /home/raq3785/bandrplus.com -s /usr/lib/sftp-server -M -N -g sftponly raq3785
Setting the Password:
sudo passwd raq3785
sudo adduser raq3785 sftponly
Step 3- Setup the users home directory
Right, lets create a home for raq3785and give him somewhere to put his files. Enter the commands below one by one on separate lines:
sudo mkdir -p /home/raq3785/bandrplus.com sudo chown root:sftponly /home/raq3785 sudo chown raq3785:sftponly /home/raq3785/bandrplus.comsudo usermod raq3785 -d /bandrplus.com
sudo chmod 755 /home/raq3785 sudo chmod 755 /home/raq3785/bandrplus.com
The first line creates the ‘/home/raq3785‘ and /home/raq3785/bandrplus.com‘ directories.
The second line sets the owner and group of the /home/raq3785 directory to root. This is an important step as the SSH server will complain (and refuse to let our restricted user login) if the root of the users home directory is NOT owned by root.
You should be able to login to you account with a username and password when you’ve completed all the steps in this guide, but it’s recommended you use the public key method for authentication as it is considerably more secure.
If you already have a private and public key you would like to use,
then all you need to do is to upload a copy of the public key to a
subdirectory named .ssh in the users home directory.
Assuming that our public key file is named ‘raq3785.pub‘, we would issue the following commands to setup public key authentication for the raq3785 user account.
cd /home/raq3785/.ssh cat raq3785.pub >> authorized_keys chmod 700 authorized_keys chown raq3785:sftponly authorized_keys rm -r raq3785.pub
Step 4- Add an entry to /etc/shells
Open the file sudo vi /etc/shells as root in your favorite text-editor, and add the following line at the bottom:
/usr/lib/sftp-server
Step 5- Amend the SSH Server Configuration file
Open the SSH server configuration file as root to start making changes. On a Ubuntu system, this file is usually
sudo vi /etc/ssh/sshd_config
this may differ with other distributions, so check beforehand.
Find the line Subsystem sftp /usr/lib/openssh/sftp-server and change it to read:
Subsystem sftp internal-sftp
Find the line UsePam yes and comment it:
Now add the following lines at the bottom of the file:
Match group sftponlyChrootDirectory /home/%u
# ChrootDirectory %h
X11Forwarding no
AllowTcpForwarding no
ForceCommand internal-sftp
Match
The line Match group sftponly tells the SSH server to apply the configuration options below it to all members of the ‘sftponly‘ system group.
The line (ChrootDirectory %h tells the SSH server to confine a user to their home directory only (The home directory is specified here using ‘%h‘)
The ‘X11Forwarding no‘ and ‘AllowTcpForwarding no‘ lines prevent the user from, respectively, accessing graphical applications on the server and from connecting to other systems via ours.
The ‘ForceCommand internal-sftp ‘ line prevents the user from executing their own commands and forces them to use the SFTP server component of the SSH server by executing the ‘internal-sftp‘ command when the user logs in.
More information on the various SSH server configuration options available and what they do can be found here.
Step 6- Restart the SSH Server
Ubuntu/Debian users can issue the following command to restart the SSH server:
sudo /etc/init.d/ssh restart
That’s it. You should be able to login using the ‘sftp‘ command with either the username and password you setup or using your private key (if you set this up in Step 2.) Using the setup outlined here, you would only have to repeat steps 1-3 to setup new accounts.
Hope this is useful to someone.
Should you run in any problems, check /var/log/syslog and /var/log/auth.log for details. Runssh or sftp with the -vvv option for debugging messages. For sftp, the
option must appear before the host as in sftp -vvv user@host.
=======================================================================
For extra security, restrict the users who can login. If you forget to add SFTP users to the sftp group, you give them free shell access. Not a nice scenario. Because SSH cannot combine AllowUsers andAllowGroups (a login has to fulfill both rules), you've to create an additional group, say ssh-users. Add the users who are allowed to login (youruser below) over SSH:
sudo groupadd ssh-users sudo usermod -a -G ssh-users youruser
And add the next line to sudo vi /etc/ssh/sshd_config
AllowGroups ssh-users sftponly
Now proceed with modifying the permissions of the users home directory to allow for chrooting (example user raq3785):
sudo chown root:sftponly /home/raq3785 sudo chmod 755 /home/raq3785
sudo chmod 755 /home/raq3785/bandrplus.com
Create a directory in which raq3785 is free to put any files in it:
sudo mkdir /home/raq3785/bandrplus.com
sudo chown raq3785: /home/raq3785/bandrplus.com
sudo chmod 755 /home/raq3785/bandrplus.com
==============================================================
==============================================================
==============================================================
### cd /home/apache/http
### ln -s /home/raq3785/bandrplus.com/ /home/apache/http/bandrplus.com
### ls -l | grep bandrplus.com
lrwxrwxrwx 1 root root 28 Feb 4 13:53 bandrplus.com -> /home/raq3785/bandrplus.com/
chown -R apache:apache /home/apache/http/bandrplus.com
chown apache:apache /home/apache/http/bandrplus.com
ln -s /home/raq3785/bandrplus.com/* /home/apache/http/bandrplus.com
— =======================================================
— =======================================================
— =======================================================
Expected results for user::::
### ls -l / | grep home
drwxr-xr-x 6 root root 4096 Feb 4 13:10 home
### ls -l /home | grep raq3785
drwxr-xr-x 4 root sftponly 4096 Feb 4 13:34 raq3785
### ls -l /home/raq3785/
total 8
drwxr-xr-x 2 raq3785 sftponly 4096 Feb 4 13:36 bandrplus.com
drwxr-xr-x 4 raq3785 sftponly 4096 Feb 4 13:27 www
### sudo cat /etc/group | grep sftp
sftponly:x:1002:apache,root,raq3785
sftpguy:x:1004:
### sudo cat /etc/passwd | grep raq3785
raq3785:x:1002:1002::/bandrplus.com:/usr/lib/sftp-server
— =======================================================
sudo service ssh start
sudo service ssh restart
sudo service ssh stop
— =======================================================
Apache with MONO
http://www.smithvoice.com/apache-logging-access-and-errors
Build ASP.NET/Mono Applications with mod_mono and Apache on Ubuntu 12.04
Published: Thursday, August 5th, 2010 by Brett Kaplan
mod_mono is an Apache module that makes it possible to run ASP.NET applications in Linux environments running Apache. While ASP.NET is a Microsoft technology and is traditionally used with IIS, mod_monohas become a viable option for deploying ASP.NET applications on Linux. This guide is largely based on the mod_mono guide from the Ubuntu Community and theMono Project's Apache and Mono documentwith minor modifications. This guide does not cover installation and configuration of the Mono IDE which is used to develop ASP.NET applications on Linux. If you are interested in developing using Visual Studio for Mono, you can download a 30-day trial of the commercial Mono Tools plugin at the Mono Tools for Visual Studio page.
This guide assumes that you've followed the steps outlined in ourgetting started guide. You will install theApache web serverwith very minimal configuration. If you already have Apache installed and configured, you may omit these steps; however, if you have not installed Apache and are unfamiliar with this server read the installation guide for additional documentation. Additionally,mod_mono is incompatible with the integrated PHP interpreter described in other guides. If you need to have both mod_mono and PHP running on the same Apache server you will need to run PHP scripts using the CGI method
Contents
Before installing mod_mono we must ensure that the universerepositories are enabled on your system. Your/etc/apt/sources.list should resemble the following (you may have to uncomment or add the universe lines):
File: sudo vi /etc/apt/sources.list
### DAQ
## main & restricted repositories
deb http://us.archive.ubuntu.com/ubuntu/ lucid main restricted
deb-src http://us.archive.ubuntu.com/ubuntu/ lucid main restricted
deb http://us.archive.ubuntu.com/ubuntu/ lucid-updates main restricted
deb-src http://us.archive.ubuntu.com/ubuntu/ lucid main restricted
deb http://security.ubuntu.com/ubuntu lucid-security main restricted
deb-src http://security.ubuntu.com/ubuntu lucid-security main restricted
## universe repositories
deb http://us.archive.ubuntu.com/ubuntu/ lucid universe
deb-src http://us.archive.ubuntu.com/ubuntu/ lucid universe
deb http://us.archive.ubuntu.com/ubuntu/ lucid-updates universe
deb-src http://us.archive.ubuntu.com/ubuntu/ lucid-updates universe
deb http://security.ubuntu.com/ubuntu lucid-security universe
deb-src http://security.ubuntu.com/ubuntu lucid-security universe
If you had to enable new repositories, issue the following command to update your package lists:
#apt-get update
sudo aptitude update
aptitude (to see what remains)
#apt-get upgrade
sudo aptitude safe-upgrade
aptitude (to see what remains)
If you already have Apache installed and configured, you can safely skip this section of the guide. Install Apache by running the following command:
sudo apt-get install apache2
As mentioned earlier, you will need to go to the installation guide if you wish to configure your server beyond the default configuration.
The Apache daemon must be stopped before mod_mono is installed. Issue the following command to stop the apache process:
sudo /etc/init.d/apache2 stop
At this point we're able to install the required packages for mod_mono. Run the following command:
sudo apt-get install mono-apache-server2 libapache2-mod-mono libmono-i18n2.0-cil
While installing, you will see a prompt that looks like the following:
Configuration file `/etc/apache2/mods-available/mod_mono.conf'
==> File on system created by you or by a script.
==> File also in package provided by package maintainer.
What would you like to do about it ? Your options are:
Y or I : install the package maintainer's version
N or O : keep your currently-installed version
D : show the differences between the versions
Z : background this process to examine the situation
The default action is to keep your current version.
*** mod_mono.conf (Y/I/N/O/D/Z) [default=N] ?
Accept the default option at this point. When the installation process completes start Apache with the following command:
sudo vi /etc/apache2/apache2.conf
ErrorLog /srv/www-logs/apache2.error.log
sudo mkdir -p /srv/www-logs
sudo mkdir -p /srv/www
sudo useradd -d /home/apache -m apache
sudo passwd apache
sudo mkdir /home/apache/.mono
sudo chown root:apache /home/apache/.mono
sudo chmod 0774 /home/apache/.mono
sudo chown root:apache /srv/www-logs/
sudo chmod 0774 /srv/www-logs/
sudo chown -R apache /srv/www/
sudo chgrp -R apache /srv/www/
sudo chmod -R 0774 /srv/www/
sudo vi /etc/apache2/envvars
export
APACHE_RUN_USER= apache
export APACHE_RUN_GROUP= apache
We recommend using name-based virtual hosts for web hosting. Refer to the Apache documentation for setting up Name-based virtual hosts.
Recent versions of mod_mono utilize the AutoHosting method of application deployment. This allows non-privileged users to deploy new applications without modifying Apache configuration files. While this provides great flexibility, it may also present a security risk. As a result, mod_mono must be enabled on a per-virtual host basis.
For the sake of this guide, we're going to create a site on the root of our example domain, example.org. If you already have an Apache configuration for the root of your site, you will need to modify your existing virtual host file or create a new one on a subdomain of your site. Create the virtual host file, taking the following example virtual host configuration and modifying it to suit your needs. You may also use the Mod_Mono Configuration Generator to generate your own custom configuration.
File excerpt:/etc/apache2/sites-available/example.org
<VirtualHost *:80>
ServerName example.org
ServerAdmin web-admin@example.org
ServerAlias www.example.org
DocumentRoot /srv/www/example.org/public_html
ErrorLog /srv/www/example.org/logs/error.log
CustomLog /srv/www/example.org/logs/access.log combined
MonoServerPath example.org "/usr/bin/mod-mono-server2"
MonoDebug example.org true
MonoSetEnv example.org MONO_IOMAP=all
MonoApplications example.org "/:/srv/www/example.org/public_html"
<Location "/">
Allow from all
Order allow,deny
MonoSetServerAlias example.org
SetHandler mono
SetOutputFilter DEFLATE
SetEnvIfNoCase Request_URI "\.(?:gif|jpe?g|png)$" no-gzip dont-vary
</Location>
<IfModule mod_deflate.c>
AddOutputFilterByType DEFLATE text/html text/plain text/xml text/javascript
</IfModule>
</VirtualHost>
Save and close the file, and create the directories referenced in theDocumentRoot and ErrorLog directive:
mkdir -p /srv/www/example.org/public_html
mkdir /srv/www/example.org/logs
Enable the site by running the a2ensite command:
a2ensite example.org
FileZilla Copy all files/directorys E:\WebSites\.NET WWW\* /home/apache/www
sudo mv /home/apache/www/*.com /etc/apache2/sites-available/
sudo mv /home/apache/www/*.Web /etc/apache2/sites-available/
sudo mv /home/apache/www/*.org /etc/apache2/sites-available/
sudo chown root:root /etc/apache2/sites-available/*
sudo mv /home/apache/www/complete/* /srv/www/
sudo –rf rm /home/apache/www/
sudo /etc/apache2/sites-available
sudo a2ensite AJ.QBytesWorld.com
sudo a2ensite Ashleigh.QBytesWorld.com
sudo a2ensite BlogEngine.Web
sudo a2ensite Gaming.BlogEngine.Web
sudo a2ensite Java.Qbytesworld.com
Agile.QBytesWorld.com
Ajax.QBytesWorld.com
QbytesWorld.com
QbytesWorld.DynDns.info
QbytesWorld.info
TFSBasicTraining.QBytesWorld.com
_bandrplus.com
sudo chown -R apache /srv/www/
sudo chgrp -R apache /srv/www/
sudo chmod -R 0774 /srv/www/
Since we have modified the virtual host configuration, Apache must be reloaded:
/etc/init.d/apache2 reload
If you still see the default "It works!" Apache installation page, you may need to disable the default site. Run the following command if this is an issue for you:
a2dissite default
/etc/init.d/apache2 reload
Note: Should you restart Apache in the future, you will see an error that will look similar to this:
[crit] (13)Permission denied: Failed to attach to existing dashboard,
and removing dashboard file '/tmp/mod_mono_dashboard_XXGLOBAL_1' failed
(Operation not permitted). Further action impossible.
You can safely ignore this warning, as it won't affect deployment using the methods explained in this guide.
Ubuntu Linux: add a new user to secondary group
Use the following syntax:
useradd -G Group-name Username
passwd Username
Create a group called foo and add user tom to a secondary group called foo:
$ sudo groupadd foo
$ sudo useradd -G foo tom
OR
# groupadd foo
# useradd -G foo tom
Verify new settings:
id tom
groups tom
Finally, set
the password for tom user, enter:
$ sudo passwd tom
OR
# passwd tom
You can add user tom to multiple groups – foo, bar, and ftp, enter:
# useradd -G foo,bar,ftp top
useradd -d /home/apache -m apache
passwd apache
mkdir /home/apache/.mono
chown root:apache /home/apache/.mono
chmod 0774 /home/apache/.mono
chown root:apache /srv/www-logs/
chmod 0774 /srv/www-logs/
groupadd apache
useradd –g apache apache
sudo chown -R apache /srv/www/
sudo chgrp -R apache /srv/www/
sudo chmod -R 0774 /srv/www/
#########################################################
### Configure the rights to YourFolder ### (optional***)
cd /srv/www/YourFolder
sudo chown -R root:www-data .
sudo chmod -R 774 .
sudo usermod -a -G www-data <yourusername>
#########################################################
cat /etc/apache2/envvars
change ENVARS user and group:
vi /etc/apache2/envvars
export
APACHE_RUN_USER= apache
export APACHE_RUN_GROUP= apache
sudo /etc/init.d/apache2 stop
rm -rf /tmp/.wapi/
sudo rm -rf /tmp/*
sudo rm -rf /srv/www-logs/*
sudo /etc/init.d/apache2 start
sudo /etc/init.d/apache2 start
sudo /etc/init.d/apache2 stop
sudo chmod -R 0777 /srv/
sudo chown -R www-data /srv/
sudo chgrp -R www-data /srv/
sudo rm -rf /tmp/*
sudo rm -rf /srv/www-logs/*
sudo /etc/init.d/apache2 start
You may wish to consult the following resources for additional information on this topic. While these are provided in the hope that they will be useful, please note that we cannot vouch for the accuracy or timeliness of externally hosted materials.
Hostname and TimeZone
Ubuntu / Debian
Enter following commands to set the hostname, replacing plato with the hostname of your choice:
echo "plato" > /etc/hostname hostname -F /etc/hostname
If it exists, edit the file /etc/default/dhcpcd to comment out the SET_HOSTNAME directive:
File excerpt:/etc/default/dhcpcd
#SET_HOSTNAME='yes'
Update /etc/hosts
Next, edit your /etc/hosts file to resemble the following example, replacing plato with your chosen hostname, example.com with your system's domain name, and 12.34.56.78 with your system's IP address. As with the hostname, the domain name part of your FQDN does not necesarily need to have any relationship to websites or other services hosted on the server (although it may if you wish). As an example, you might host "www.something.com" on your server, but the system's FQDN might be "mars.somethingelse.com."
File:/etc/hosts
127.0.0.1 localhost.localdomain localhost
12.34.56.78 plato.example.com plato
If you have IPv6 enabled on your Linode, you will also want to add an entry for your IPv6 address, as shown in this example:
File:/etc/hosts
127.0.0.1 localhost.localdomain localhost
12.34.56.78 plato.example.com plato
2600:3c01::a123:b456:c789:d012 plato.example.com plato
The value you assign as your system's FQDN should have an "A" record in DNS pointing to your Linode's IPv4 address. For Linodes with IPv6 enabled, you should also set up a "AAAA" record in DNS pointing to your Linode's IPv6 address. For more information on configuring DNS, seeAdding DNS Records.
Setting the Timezone
All Linodes are set to Eastern Standard Time by default, but you can change the timezone to whatever you want it to be. It may be best to set it to the same timezone of most of your users. If you're unsure which timezone would be best, consider using universal coordinated time or UTC (also known as Greenwich Mean Time).
Checking the Time
Now try entering the following command to view the current date and time according to your server:
date
The output should look similar to this: Thu Feb 16 12:17:52 EST 2012.
### Installed Ubuntu Server 12.04 ###
Download here.
Installed Ubuntu Server 12.04
- openSSH, if not from Install click here.
Disable CTL-ALT-DEL
- here.
HostName and TimeZone
Apply Patches
sudo pico /etc/apt/sources.listdeb http://ro.archive.ubuntu.com/ubuntu hoary universedeb-src http://ro.archive.ubuntu.com/ubuntu hoary universe
sudo add-apt-repository ppa:sun-java-community-team/sun-java6sudo add-apt-repository ppa:chromium-daily/stablesudo apt-get update- sudo apt-get update
- sudo aptitude safe-upgrade
- –
- Security patching only via Unattended Upgrades.
Audit/Log user activity.
Disks and mounts.
- Mount and Format disk…here.
- NFS – NetWork File Share, (Linux/UNIX only).
- Samba File Share, (If windows needs access, click here).
Backup Jobs.
- Job here.
- $ sudo apt-get install nmon –> here.
- $ sudo apt-get install htop –> here.
- Install sensors for monitoring –>here.
Xosview –> here.
Ability to Search for packages
sudo apt-get install aptitudesudo aptitude search <package part>
Application Setup
- Java setup here.
- WebMin here and info here.
- VirtualBox
- Apache2
-
Tomcat
- Tomcat Multi instance apt-get config here.
- Tomcat Multi instance manual config here.
- Connect with JMX here.
- https://java.qbytesworld.com/post/Tomcat-and-Apache-Setup-With-LB.aspx
Secure the server:
http://library.linode.com/securing-your-server
High availability Ubuntu servers
FTP
SSH should work for most needs (Filezilla), but if FTP is needed
CRONTAB
- Setup backups here.
- Clean scripts
- etc….
Startup/Shutdown script
- How to setup here.
Update and Patch
- How to update and patch here.
How do I host Java application using Apache AJP connector
http://www.serveridol.com/2011/03/18/how-do-i-host-java-application-using-apache-ajp-connector/
=============================================
Here I’m going to host a java application on my development server which had capable of hosting php/rails sites.
For hosting a Java application, You may complete the following steps.
Packages required
1.mod_jk apache module <
2. Tomcat 6.0.29
3. JDK 1.6.0_14
4. Apache 2.2.3
1. Install mod_jk
Download the the mod_jk built for your Apache version from here http://download.filehat.com/apache//tomcat/tomcat-connectors/jk/binaries/linux/ and copy it to /usr/lib/httpd/modules/ and rename it to mod_jk.so
[root@rc-040 conf]# ls -la /usr/lib/httpd/modules/mod_jk.so
-rw-r–r– 1 root root 416473 Nov 1 10:12 /usr/lib/httpd/modules/mod_jk.so
Now I’m going to create a jk.conf file and workers.properties in “/etc/httpd/conf.d”
#vi /etc/httpd/conf.d/jk.conf
LoadModule jk_module /usr/lib/httpd/modules/mod_jk.so
JkWorkersFile /etc/httpd/conf.d/workers.properties
JkShmFile /var/log/httpd/mod_jk.shm
JkLogFile /var/log/httpd/mod_jk.log
JkLogLevel info
JkLogStampFormat “[%a %b %d %H:%M:%S %Y] ”
#vi /etc/httpd/conf.d/workers.properties
worker.list=worker1
# Set properties for worker1 (ajp13)
worker.worker1.type=ajp13
worker.worker1.host=localhost
worker.worker1.port=8009
# service httpd restart
2. Install Java and Apache Tomcat
I installed Java in ” /usr/java” and tomcat in “/usr/local” and set a permanent environment variable for JAVA_HOME and CATALINA_HOME by copying following variables in s script. My java.sh having
a. Setting up Java variables
# vi /etc/profile.d/java.sh
JAVA_FONTS=/usr/share/fonts/truetype
ANT_HOME=/usr/share/ant
JAVACC_HOME=/usr/java/javacc
SPRING_HOME=/usr/local/spring-framework-1.1.4
CLASSPATH=.:$JAVA_HOME/lib
CATALINA_BASE=/usr/local/apache-tomcat-6.0.29
CATALINA_HOME=/usr/local/apache-tomcat-6.0.29
CATALINA_TMPDIR=/usr/local/apache-tomcat-6.0.29/temp
JBOSS_HOME=/usr/local/jboss-4.0.3SP1
PATH=$JAVA_HOME:$JAVA_HOME/bin:$JAVACC_HOME/bin:$ANT_HOME/bin:$CATALINA_HOME/bin:$JBOSS_HOME/bin:ANT_HOME/bin:/usr/local/godesk/usr/bin:$PATH
PKG_CONFIG_PATH=/usr/local/lib/pkgconfig/glib-2.0.pc
export PKG_CONFIG_PATH
LD_LIBRARY_PATH=/usr/local/lib;export LD_LIBRARY_PATH;
export PATH JAVA_HOME JAVA_FONTS ANT_HOME JAVACC_HOME CATALINA_BASE CATALINA_HOME CATALINA_TMPDIR JBOSS_HOME
export CLASSPATH
# cp java.sh /etc/profile.d/
# source /etc/profile.d/java.sh
[root@rc-040 public_html]# echo $JAVA_HOME $CATALINA_HOME
/usr/java/jdk1.6.0_14 /usr/local/apache-tomcat-6.0.29
Perfect !
b. Configuring Tomcat
Ajp connector will enabled by default in Tomcat which running on the port 8009 ( check the server.xml file). Ensure that follwoing lines are commented out.
Now you need to Add virtual Host entry in Tomcat server.xml file. Open “/usr/local/apache-tomcat-6.0.29/conf/server.xml” and find the line starts with <Engine name=”Catalina” . Add the following entry after this line and restart the tomcat.
<Engine name=”Catalina” defaultHost=”localhost”>
<Host name=”dplpool.rainconcert.in” appBase=”/home/dplpool/public_html”
autoDeploy=”true” unpackWARs=”true”
xmlValidation=”false” xmlNamespaceAware=”false” >
<Alias>selfcare.rainconcert.in</Alias>
< Context path=”/newapp” docBase=”.”/>
< /Host>
Here are the description of each parameter given,
1. name : Your domain name
2. appBase : Where .war file to be placed (it would be a ftp location in most cases)
3. autoDeploy : This is ideal for development purpose and must be set to “false” in Prod enviorment
4. unpackWAR : Tomcat is exploded the war if it is set to true file by looking for if any class file changes in “WEB-INF” folder
5. Alias : Domain alias, can added any number of domains to use the same hosting space
6. Context path : Like location alias in Apache. Suppose if you want to access the images over the http://domain.tld/images, you need to set in this virtual host
3. Apache Configuration.
I have placed a virtualhost config. file (javapp.conf” under “/etc/httpd/conf.d” having the following content.
< VirtualHost *:80>
ServerName domain.tld
ServerAlias www.domain.tld
DocumentRoot /home/dplpool/public_html
DirectoryIndex index.html
Alias / /home/dplpool/public_html
ErrorLog logs/myapp-javahost.log
JkMount /*.jsp worker1
JkMount /* worker1</VirtualHost>
NB: You need to usr the exact identical hostname in Apache virtualhost and Tomcat virtual host. Otherwise AJP connector can’t identify the workers which JkMount being looked for.
Restart Apache and Tomcat
Testing new hosting,
You can download the sample java application provided by the Apache project. Download this file http://tomcat.apache.org/tomcat-7.0-doc/appdev/sample/sample.war and rename it to ROOT.war. Then upload it to “/home/domain/public_html”. You will see the site at http://domain.tld